Taiwan Mask Corporation has established a comprehensive information security management system and strictly adheres to the requirements of the ISO 27001 information security management system. Appropriate protective measures are implemented for critical information assets within the scope of the company's information security management system. Through annual information security management review meetings, the company effectively assesses clients' expectations regarding the confidentiality, integrity, and availability of assets, ensuring the smooth and secure execution of all business operations, providing excellent service to clients, and meeting their needs.
We are committed to providing a reliable and secure information security operating environment, maintaining the legal use of information systems and data, meeting customer needs, ensuring the continuous operation of the company's critical services, and achieving the company's information security management goals. Taiwan Mask Group's responsibility for the safekeeping of customers' confidential information and its confidentiality agreements guarantee that confidential information will not be disclosed to any third party in any way.
Information Management Department
Taiwan Mask Corporation has completed its fourth annual audit and verification assessment of the ISO 27001 Information Security Management System.
Implement the 2024 Information Security Protection Plan, focusing on improvement efforts addressing information security issues. ■ Network Security: Network upgrades, social engineering drills, penetration testing ■ System Security: Regular vulnerability scanning, replacement of EOS computers, WSUS system updates ■ Application Security: Endpoint protection monitoring and legal software policy updates, antivirus upgrades, internal and external ERP management ■ Data Encryption and Authentication: SSL certificate updates, password strengthening policies ■ Physical Security: Monitoring system integration and control room setup, factory three-way gate installation, server room cabinet reinforcement ■ Backup Plan: Implement the 321 backup principle to ensure effectiveness and prevent ransomware attacks.
New two-factor authentication mechanism, password strengthening policy, factory connection restriction firewall implementation, surveillance system expansion and central control room construction, implementation of internal and external EDR control mechanisms, factory access gate construction, control of camera equipment, network A10 upgrade, and server room cabinet reinforcement.
Taiwan Mask Group's | ||
|---|---|---|
Targets set for 2023 | 2024 performance | Future goals |
Short-term goals (2025) | ||
| There were 0 incidents of improper data disclosure related to the control of business (information) services. |
|
|
| 0 incidents of data tampering or unauthorized access. |
|
|
| Information infrastructure availability reached 99.83%. |
99.84% |
|
| Information system and data backup execution rate reached 99.99%. |
99.99% |
|
| Account password settings meet the requirements 99.99% of the time. |
99.99% |
|
|
|
|
-
2024 Action Plan and Performance
We collaborated with Chunghwa Telecom to conduct information security penetration testing to assess the security vulnerabilities of the company's internal network environment, locate system weaknesses, patch vulnerabilities, and optimize security to strengthen the overall information security system. The purpose of penetration testing is to simulate the thinking of hackers and malicious users, attempting to compromise the company's website, information systems, or equipment, analyze the risk level of the test targets, and assess whether security needs to be strengthened. The test system used was Power BI-SQL (Vrfab), executed remotely/in a black-box manner. The results revealed three vulnerabilities: one medium-risk vulnerability and two low-risk vulnerabilities, with no high-risk vulnerabilities.
-
Information security management measures and management procedures formulation and annual audit
Adhering to the core cybersecurity policy of "providing a reliable and secure operating environment, maintaining the legal use of information systems and data, ensuring the continuous and normal operation of company services, and achieving the company's information security management goals," we are committed to protecting customer information privacy and the company's operational security. We regularly complete annual audits and verifications of the ISO/IEC 27001:2013 international standard for information security management systems. Between 2022 and 2024, no violations of information security regulations or customer privacy complaints were found.
To ensure the effective operation of its information security management system, Taiwan Photomask has established a series of standards, operating procedures, and auditing mechanisms. It conducts internal security audits and third-party external audits at least once a year, performs security vulnerability scans to identify and improve high-risk projects, and regularly conducts disaster drills to ensure that emergency response plans can function effectively in the event of unforeseen circumstances.
In addition to joining the Taiwan Computer Network Crisis Management and Coordination Center (TWCERT/CC), Taiwan Shield has developed an information security protection plan. To effectively respond to incidents, following the information security incident management procedure, it issues information security incident rectification forms and conducts monthly information security meetings to exchange information with various departments, collecting customer feedback and user needs for continuous improvement. To quickly resolve information security incidents and minimize their impact, Taiwan Mask Corporation has established an information security incident management procedure specifically for recording, processing, and managing these incidents. Through regular risk assessments, appropriate corrective and preventative measures are developed and implemented for high-risk services to reduce the probability of occurrence or mitigate their impact. Furthermore, an annual management review meeting is held to review the operation of the information security management system and evaluate and improve the maintenance and operation of various documents.
Implement a cybersecurity classification system. ■ General (Security P): Information not classified as confidential, but held or owned by the Company. ■ Controlled (Security C): Information valuable to the Company's business or technology; unauthorized disclosure would cause immediate or direct damage to the Company's or a third party's business operations or corporate image. ■ Confidential (Security B): Information of significant value to the Company's business or technology; unauthorized disclosure would cause immediate or direct damage to the Company's or a third party's business operations or corporate image. ■ Top Secret (Security A): Information of decisive value to the Company's business or technology; unauthorized disclosure would cause immediate or direct damage to the Company's or a third party's business operations or corporate image.
-
Information security incident handling
To effectively record, process, and manage information security incidents, and to rapidly mitigate their impact, Taiwan Photomask has established a standard reporting procedure for major information security incidents. The process for handling information security incidents includes: identifying and recording the incident, classifying and assessing its severity, notifying relevant departments and initiating action, reviewing the causes of the incident, and developing preventative measures. In handling and tracking these incidents, it is essential to first ensure that the incident has been properly resolved, and then to thoroughly analyze its causes to reduce the likelihood of similar incidents recurring.
When the Information Management Department discovers a suspected information security incident, it will immediately notify the information system manager for assistance in assessment. If confirmed as an information security incident, the Information Management Department will promptly notify department managers through the system and require them to complete the handling and response within a specified timeframe. Upon receiving the report, the Cybersecurity Task Force will use the online approval system to control and track the incident. In the event of a major information security incident, it must be reported within two hours, and in accordance with the information security management guidelines for listed companies, the Chief Cybersecurity Officer will release relevant important information to the public.
Information Environment Security
TMC is committed to maintaining the security of the information environment to provide excellent service to customers and meet their needs. Through the annual information security management review, we effectively assess customer expectations for the confidentiality, integrity, and availability of assets. This is done to achieve the information security management goal of "ensuring the confidentiality, integrity, and availability of information assets in compliance with legal, regulatory, and contractual requirements and providing continuously available services." This ensures that all business operations proceed smoothly and securely.
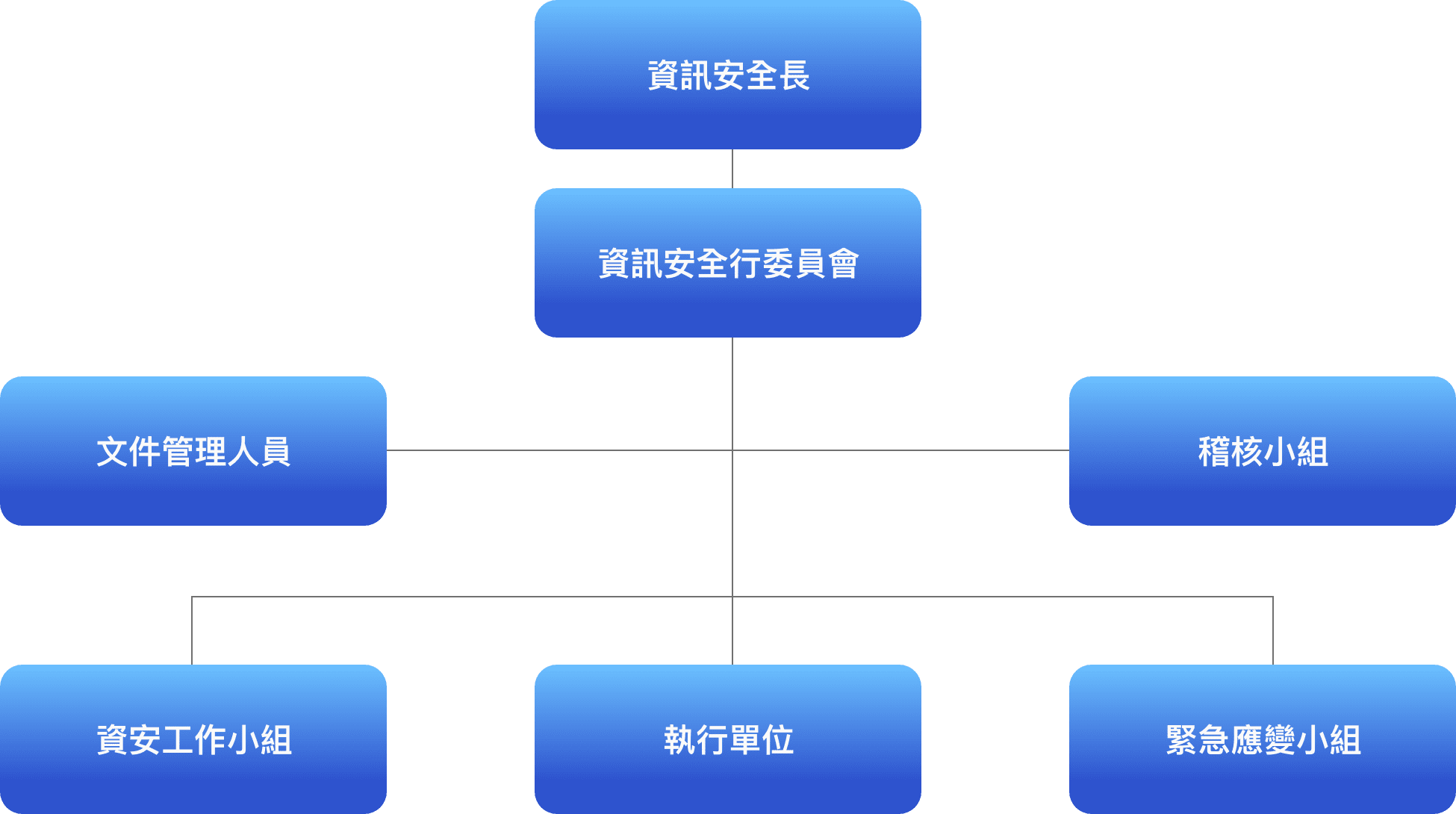
TMC's Information Security Policies provide a reliable information security operating environment, maintain the legal use of information systems and data, ensure a continuous normal operation of company services, and achieve the company's information security management objectives. This ensures the security and privacy of customer information and sustainable operations.
TMC joined the Taiwan Computer Emergency Response Team / Coordination Center (TWCERT/CC) and formulated an information security protection plan, which is implemented and reviewed annually by the Information Management Department.
To promote the importance of information security and goals related to TMC, all new employees will undergo a one-hour cybersecurity training session with a corresponding assessment. In 2022, all employees have completed one hour of cybersecurity education training, achieving a 100% completion rate and a test accuracy rate of 90% or above.
To protect customer information, encryption is employed for storage, and data is stored in a highly restricted area. All visitors and vendors entering the premises must be accompanied by authorized personnel. If there are devices with camera functionality, they must have a security sticker affixed to the lens. Additionally, peripheral devices such as USB drives, external hard drives, and mobile phones are not allowed to connect to the company's network and information equipment without authorization. To prevent data loss and damage, TMC has established a backup 3-2-1 principle. This principle dictates that data should be backed up in three copies, using two or more different backup media, with one copy stored offsite.
Most of TMC's products are customized according to customer requirements. TMC has obtained ISO/IEC 27001 certification for its information security management system. All servers are equipped with necessary security measures, including firewalls, network segmentation, and antivirus systems. Access to customer-related systems and sensitive data is restricted according to access control policies, preventing unauthorized personnel from using them. There have been no complaints or incidents violating customer privacy from 2020 to 2022.

